Analyzing and Decrypting TLS with Wireshark

Capture Session Keys (LINUX)
Open a terminal and set the SSL keylogger variable for this session (do not add this permanently, e.g. to .zshrc):
export SSLKEYLOGFILE=/home/my-user/Documents/tls_keylog.log
Now start chromium, chrome or firefox by typing the application name into your terminal and pressing enter. Just opening the browser should trigger a few key exchanges. But you can also browse the web and then check the log file:
tls_keylog.log
CLIENT_HANDSHAKE_TRAFFIC_SECRET ccda30d136b2...
SERVER_HANDSHAKE_TRAFFIC_SECRET ccda30d136b2...
CLIENT_TRAFFIC_SECRET_0 ccda30d136b2ea601eb...
SERVER_TRAFFIC_SECRET_0 ccda30d136b2ea601e...
We can now use the captured keys to decrypt our web traffic with wireshark.
Decrypt HTTPs Session in Wireshark
I now open the web interface of my INSTAR IP camera while logging the web traffic in Wireshark. Here I can see a lot of TCP and TLSv1.3 packets coming through:
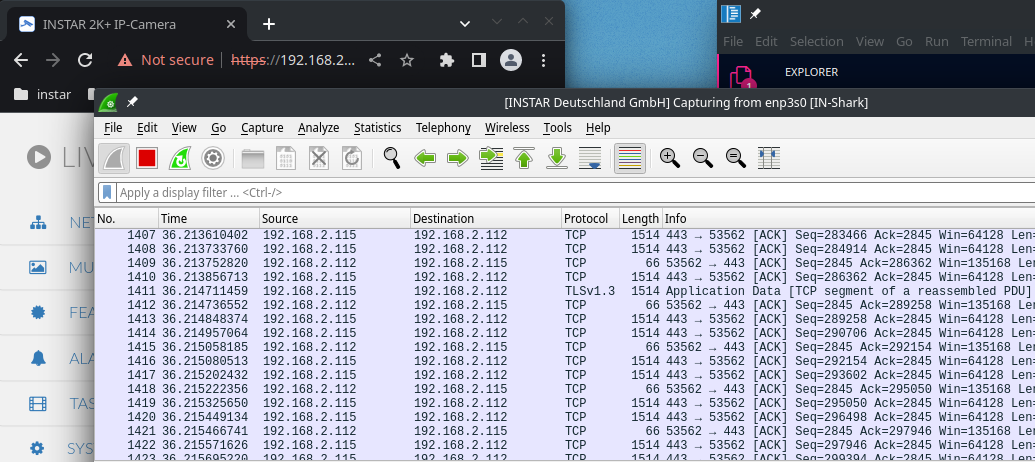
Now close the browser and stop the Wireshark capture. To clean up the log I can filter for frames that contain the IP address of my IP camera:
ip.addr == 192.168.2.115
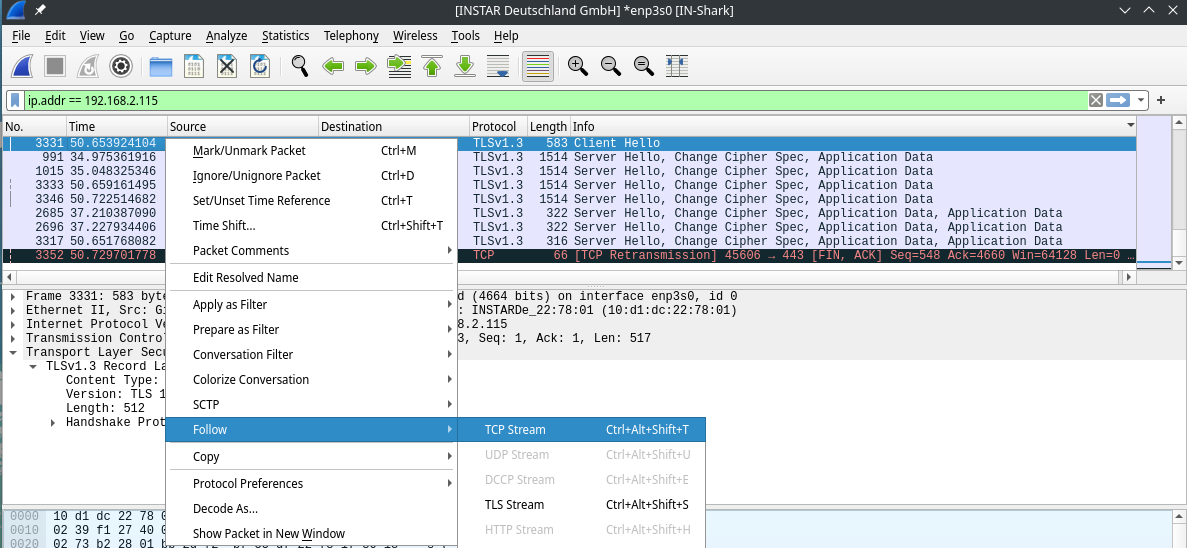
Right click one of the Client Hello packages and select to follow the TCP Stream:
Close the opening window and select the first package that contains Application Data after the hello and cypher negotiation:
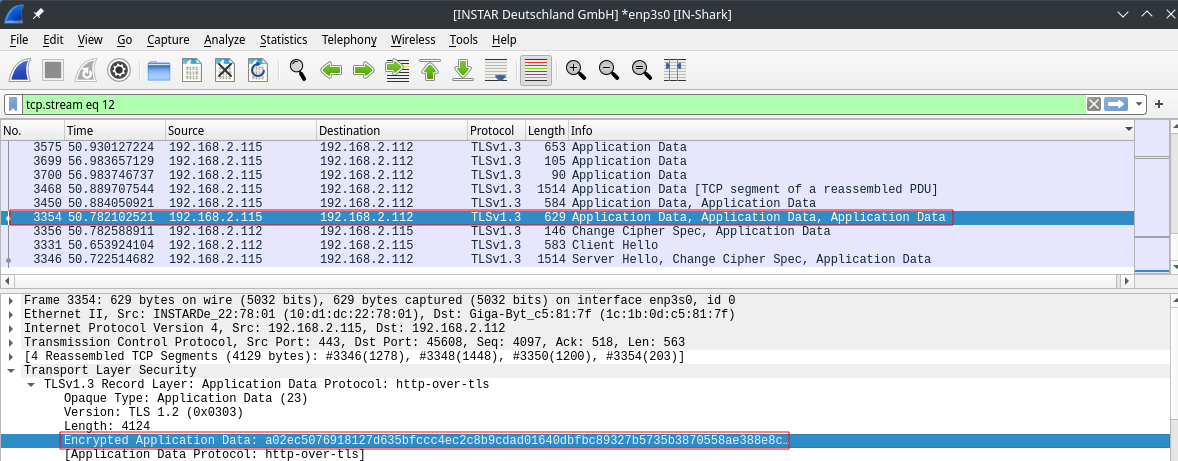
Right-click the package and open the Transport Layer Security Preferences:
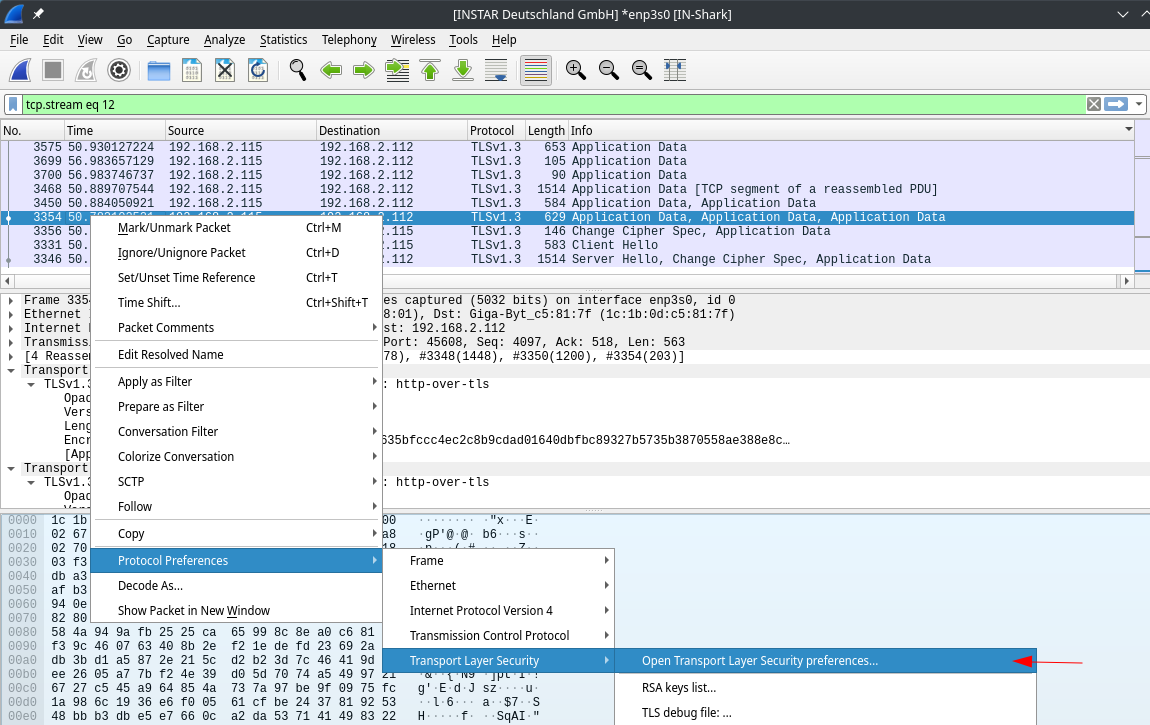
Here you need to add the log file created earlier:
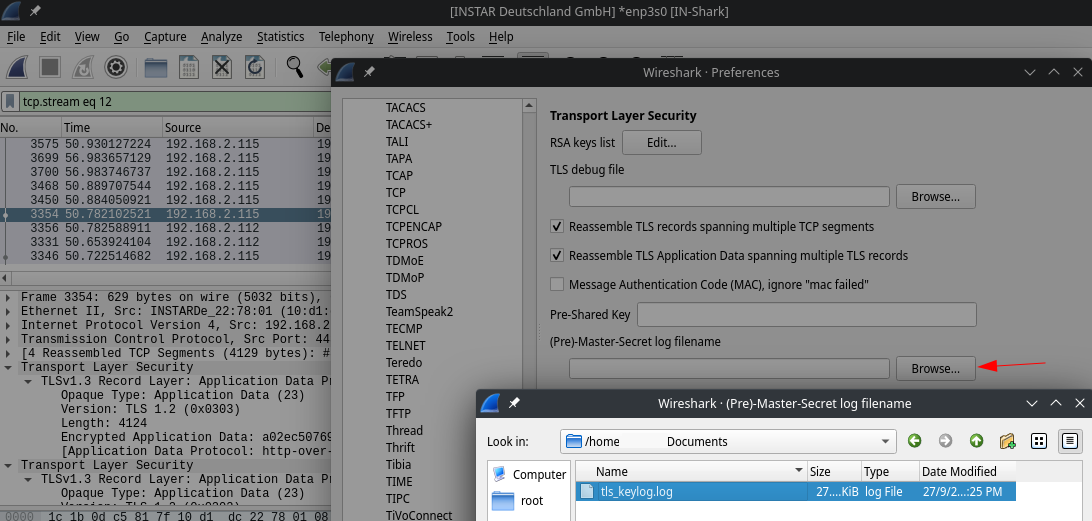
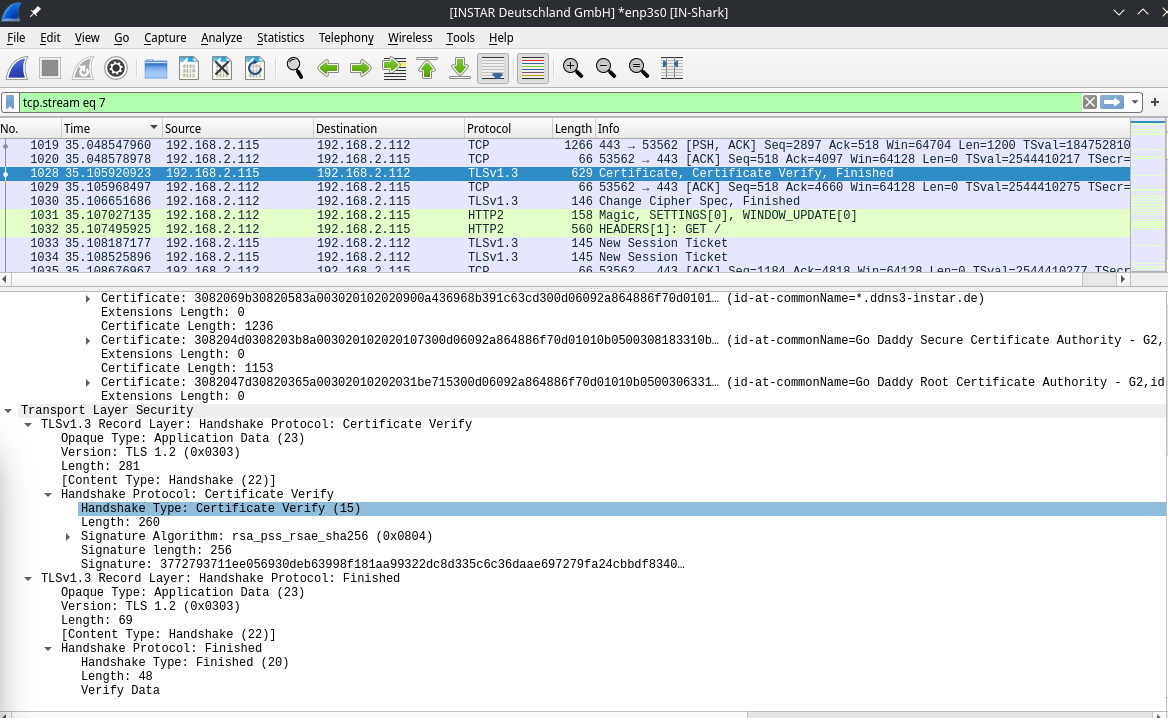
The entries are now successfully decrypted and what showed up as encrypted application data before can now be identified as a TLS handshake:
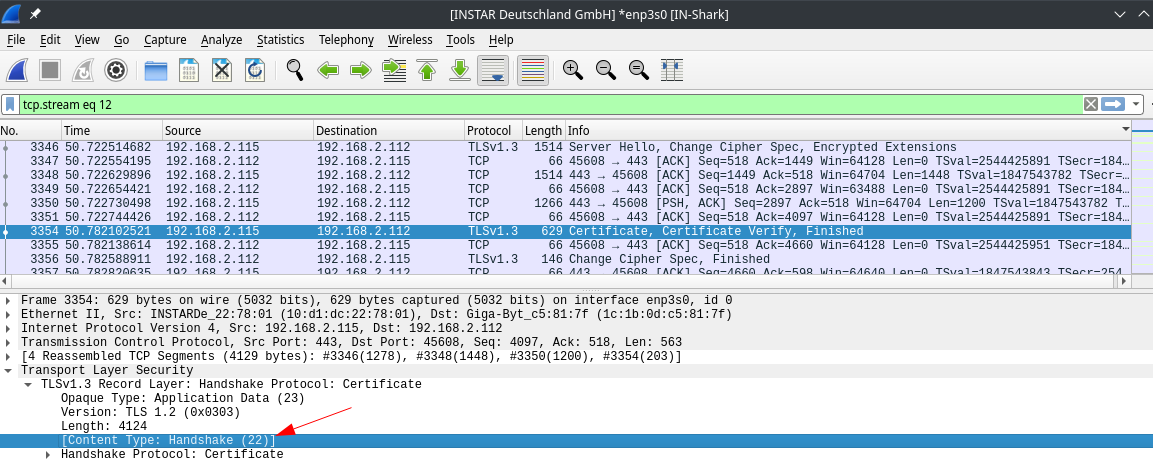
TLSv1.3 Handshake
see also tls13.xargs.org
To deeper analyze our now decrypted data we can open the Conversations window:
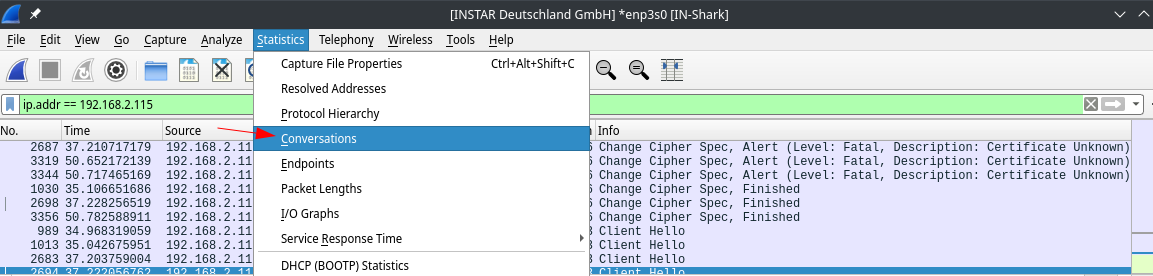
Select a "conversation" and use it to filter our log file:
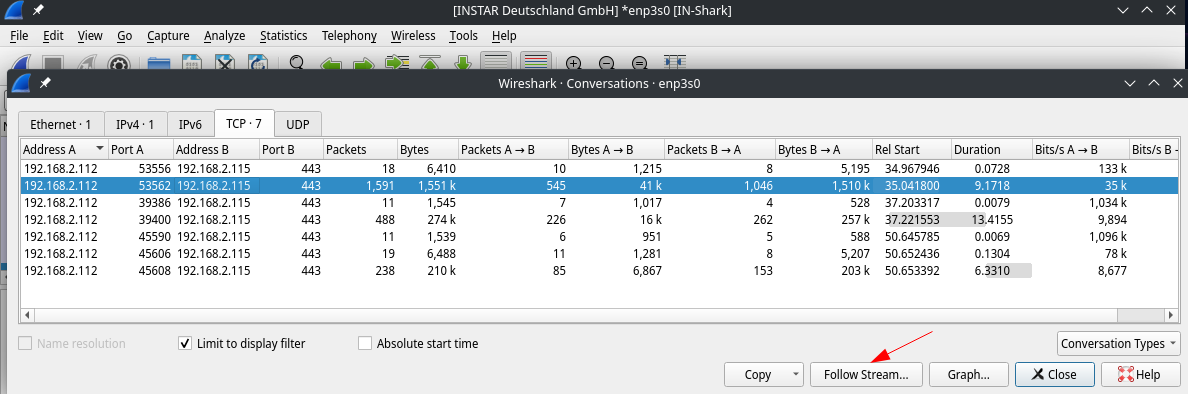
Client Hello
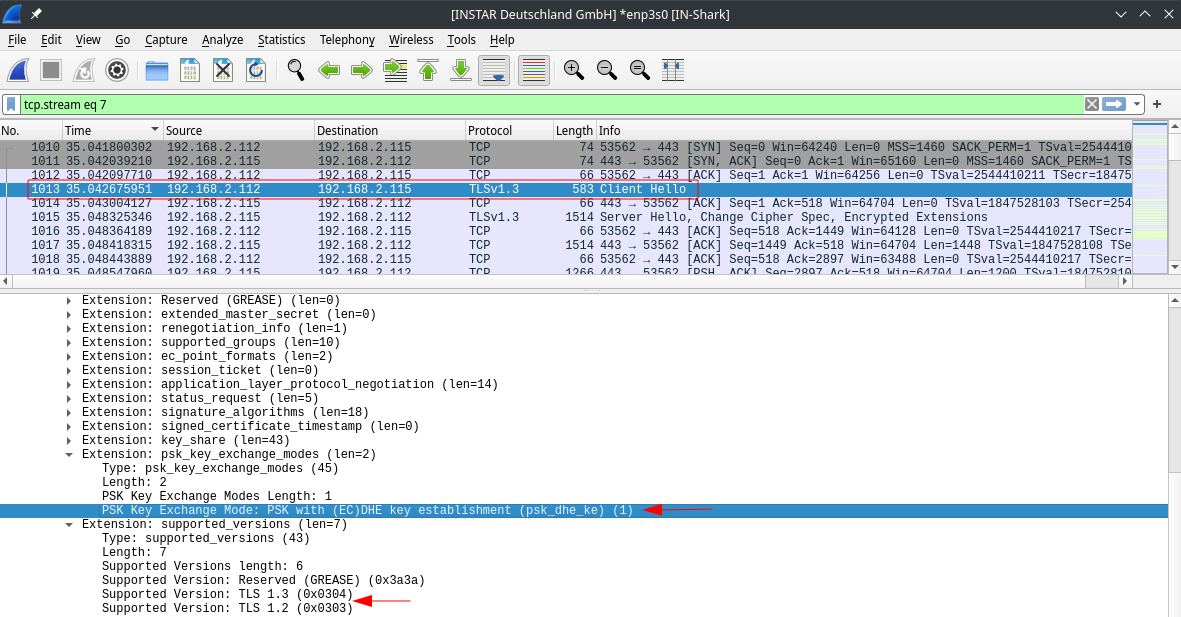
The conversation starts with a TCP handshake that is followed by a Client Hello. In here our client - in this case our web-browser - states that it knows TLSv1.3 and TLSv1.2 and insists on the Elliptical Curve Diffie Hellman Ephemeral (ECDHE) Key Exchange and supports 16 different cypher suits for the data encryption:

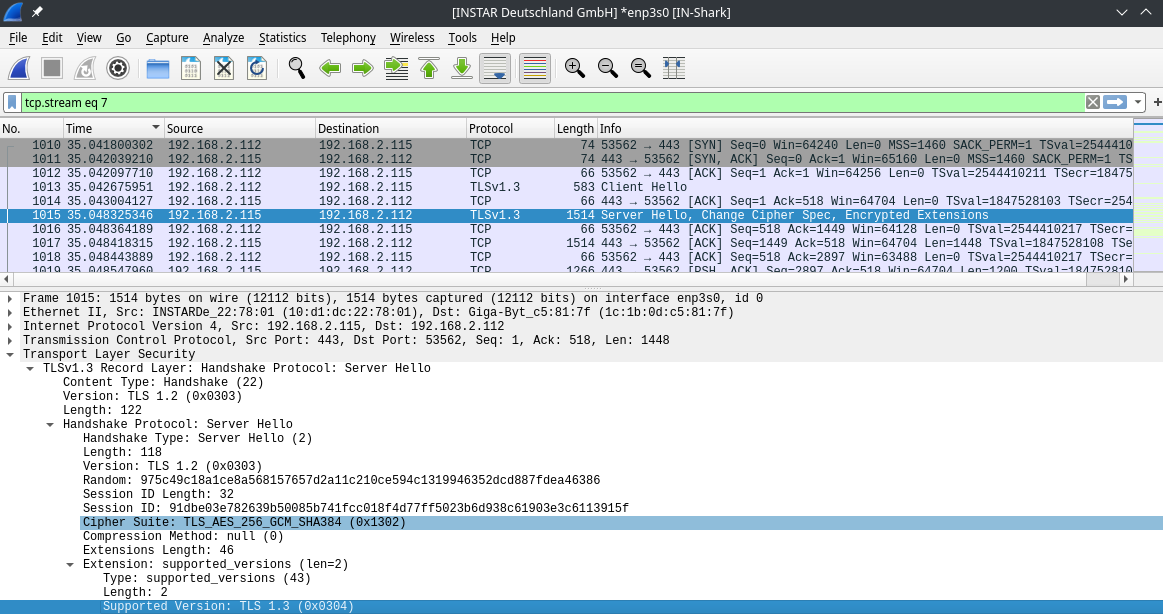
Server Hello
The server (my IP camera) - now knowing what our client (the browser) supports - picks a TLS version, cypher suite and ellipsis it wants to use - Supported Version: TLS 1.3 (0x0304), Cipher Suite: TLS_AES_256_GCM_SHA384 (0x1302) and Group: x25519 (29) - and sends it's public key:

Once the encryption is established the server will send it's TLS certificate: