Hashicorp Vault - Secrets & Tokens

In the previous step I installed Hashicorp Vault, configured it and unsealed it - so I am now ready to start using it:
vault status
Key Value
--- -----
Seal Type shamir
Initialized true
Sealed false
Total Shares 5
Threshold 3
Version 1.8.2
Storage Type consul
Cluster Name vault-cluster-c09dbd91
Cluster ID fbd3d3c4-bfed-45b3-f930-9bd1fc17c3a7
HA Enabled true
HA Cluster https://192.168.2.110:8201
HA Mode active
Active Since 2021-09-14T03:54:27.968463561Z
Adding Secrets to the Consul K/V Store
Create a Secrets Engine
Add a secrets engine to the K/V store by defining the path name and type kv:
vault secrets enable -path=thisisatest -description='This is a Test!' kv
Success! Enabled the kv secrets engine at: thisisatest/
Verify that the path was generated:
vault secrets list
Path Type Accessor Description
---- ---- -------- -----------
thisisatest/ kv kv_eb9cbb20 This is a Test!
And remove the secrets engine with:
vault secrets disable thisisatest
Success! Disabled the secrets engine (if it existed) at: thisisatest/
Add a Secret
PUT: Add a secret to your secret engine:
vault kv put thisisatest/elastic_master_login password=nIgXI6mKxt3lHmtvJEgypaE
Success! Data written to: thisisatest/elastic_master_login
GET: Read a secret from your secret engine:
vault kv get thisisatest/elastic_master_login
====== Data ======
Key Value
--- -----
password nIgXI6mKxt3lHmtvJEgypaE
DELETE: Remove a secret from your secret engine:
vault kv delete thisisatest/elastic_master_login
Success! Data deleted (if it existed) at: thisisatest/elastic_master_login
Authentication Methods
Working with Tokens
Currently, I am using the bootstrap root token that was generated when I initialized Vault. To be able to interact with the Vault API you can create additional tokens with:
vault token create
Key Value
--- -----
token s.mP10AAvC0ZdW6WinL49rGGXX
token_accessor JTFRs2OwKTLEDfJPIlGbHun7
token_duration ∞
token_renewable false
token_policies ["root"]
identity_policies []
policies ["root"]
And manually revoke them, when no longer needed:
vault token revoke s.mP10AAvC0ZdW6WinL49rGGXX
Success! Revoked token (if it existed)
Working with Username and Passwords
Activate the authentication method:
vault auth enable userpass
Success! Enabled userpass auth method at: userpass/
And add user logins to the K/V store:
vault write auth/userpass/users/manfred_mustermann password=strongpassword
Success! Data written to: auth/userpass/users/manfred_mustermann
And use the new user to login to Vault:
vault login -method=userpass username=manfred_mustermann
Password (will be hidden): strongpassword
Success! You are now authenticated. The token information displayed below
is already stored in the token helper. You do NOT need to run "vault login"
again. Future Vault requests will automatically use this token.
Key Value
--- -----
token s.kWg9HwLETHCVhHqivVUpnm1l
token_accessor BCDUSKAI3pXXVDzjQKW15nG1
token_duration 768h
token_renewable true
token_policies ["default"]
identity_policies []
policies ["default"]
token_meta_username manfred_mustermann
Working with Github Logins
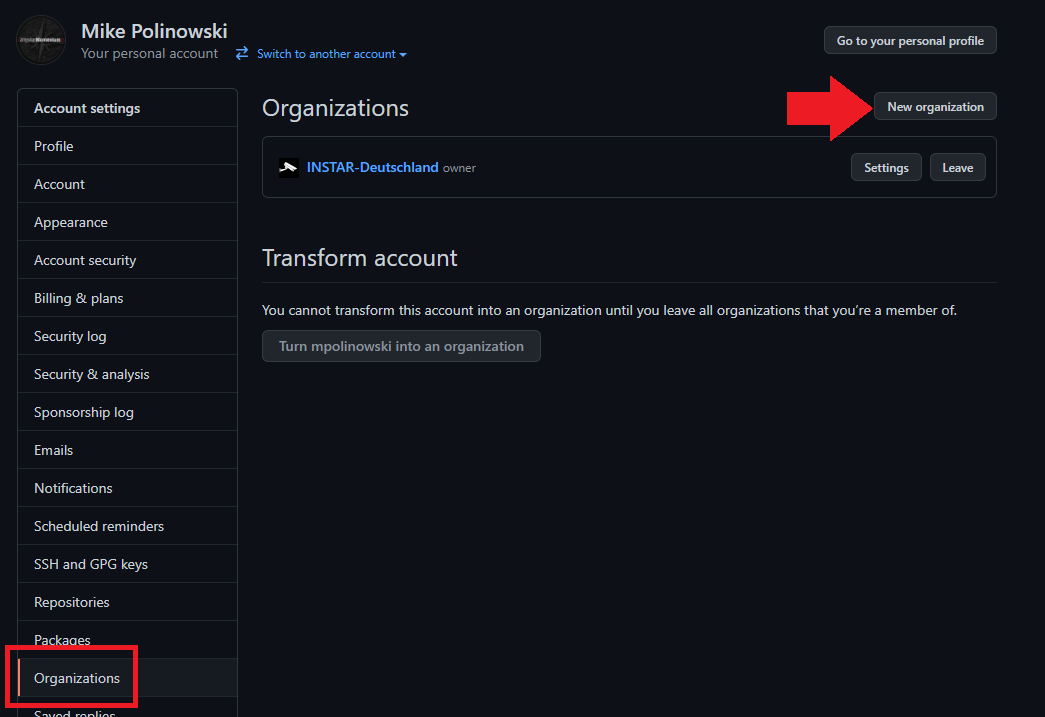
Login to your Github account and create a (free) organization from the Settings/Organization tab:
Enable Github Auth in Vault:
vault auth enable github
Success! Enabled github auth method at: github/
And add your Github organization to Vault:
vault write auth/github/config organization=INSTAR-Deutschland
Success! Data written to: auth/github/config
Assign a default tag for the authentication token. This can later be mapped to a group policy to restrict access:
vault write auth/github/map/teams/development value=gh-policy
Success! Data written to: auth/github/map/teams/development
Add a user (that is part of your Github organization) and assign a tag for a user policy:
vault write auth/github/map/users/mpolinowski value=developer-policy
Success! Data written to: auth/github/map/users/mpolinowski
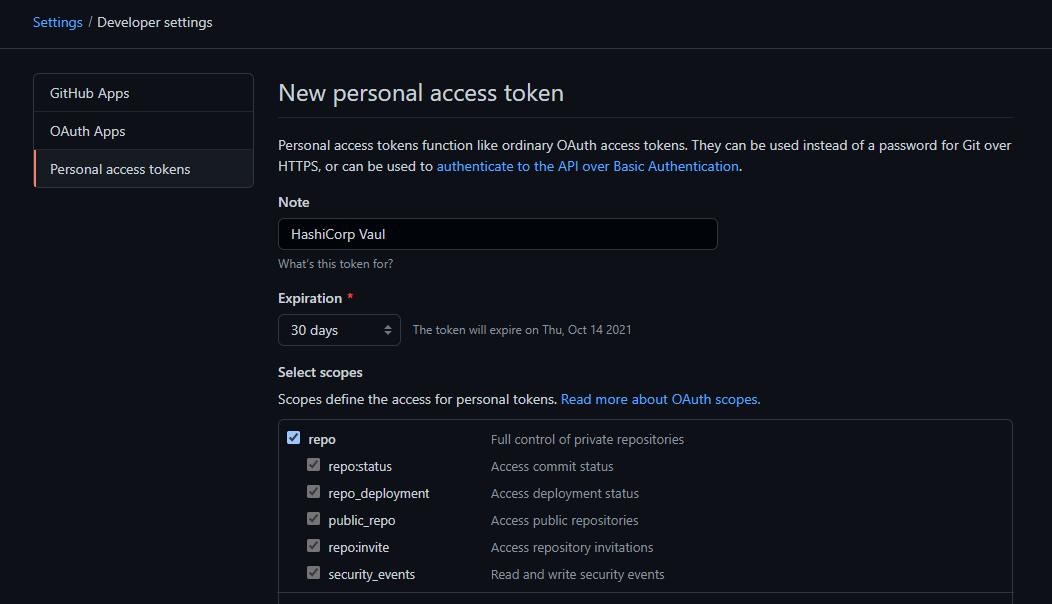
Back inside your Github Settings open the Developer tab and create a new access token:
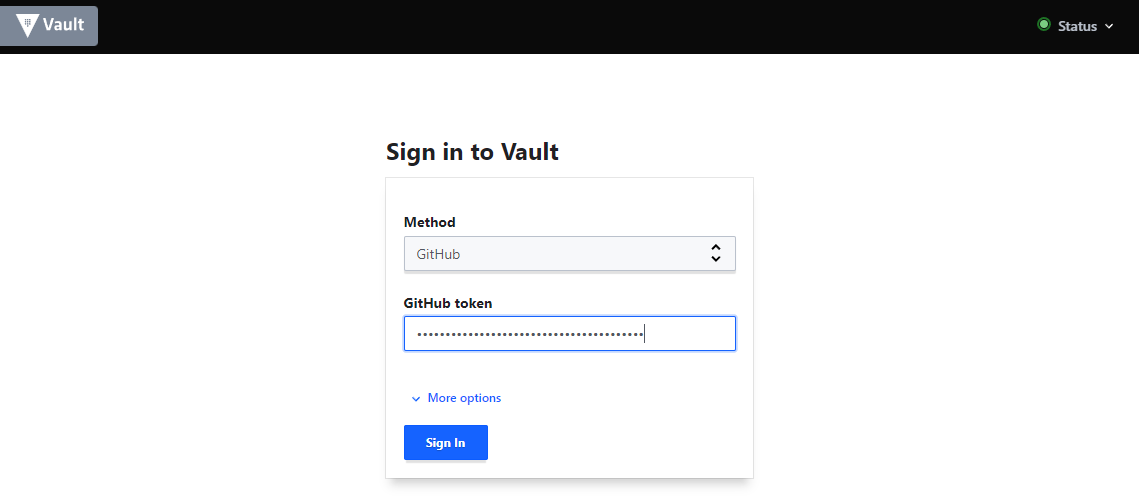
On the Vault UI choose Github as your authentication method and paste in your generated access token to have Vault veriy that you are one of the added Github users and are part of the organization that you added to Vault:
And there you go:
List all active Auth Methods
vault auth list
Path Type Accessor Description
---- ---- -------- -----------
github/ github auth_github_141b7ec9 n/a
token/ token auth_token_e36baf76 token based credentials
userpass/ userpass auth_userpass_51025fe5 n/a
Disable methods that you no longer need:
vault auth disable github
vault auth disable userpass