Hashicorp Vault - Rest API

The Vault HTTP API gives you full access to Vault via HTTP. Every aspect of Vault can be controlled via this API. The Vault CLI uses the HTTP API to access Vault.
All API routes are prefixed with
/v1/
Accessing the REST API
In the previous step I created a token s.GZHF5D5zYJk1zmzxLmxivPY8 that allowed me to read the key/value on the path secret/login/elastic using the Vault CLI::
vault kv get secret/login/elastic
====== Data ======
Key Value
--- -----
password Hzo3aku+S37JDzeXGUxZX+H5WE
To do the same with an HTTP GET request:
curl \
-H "X-Vault-Token: s.GZHF5D5zYJk1zmzxLmxivPY8" \
-X GET \
http://192.168.2.110:8200/v1/secret/login/elastic | jq
{
"request_id": "84ee50f2-78ec-96ed-ffc7-432e9bb94e74",
"lease_id": "",
"renewable": false,
"lease_duration": 2764800,
"data": {
"password": "Hzo3aku+S37JDzeXGUxZX+H5WE"
},
"wrap_info": null,
"warnings": null,
"auth": null
}
To update an existing value I can use the PUT request:
curl \
-H "X-Vault-Token: s.GZHF5D5zYJk1zmzxLmxivPY8" \
-H "Content-Type: application/json" \
-X PUT \
-d '{"password":"the_new_password"}' \
http://192.168.2.110:8200/v1/secret/login/elastic
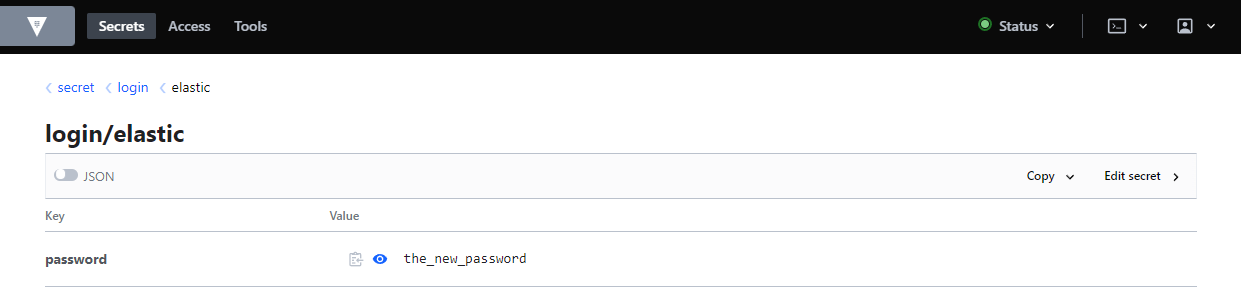
And the value is updated:
Working with Payload Files
With the root token we are now also able to do administrative work like creating new user token. First let's create a JSON file that holds all the instructions:
tee test-user-token.json <<EOF
{
"policies": ["root"],
"meta": {
"user": "test-user"
},
"ttl": "1h",
"renewable": true
}
EOF
Now we can use the POST request to add this user token by authenticating with our root token to access the /auth route:
curl \
-H "X-Vault-Token: s.TFCSNUDRJbuBGjOkgaqSfEQR" \
-X POST \
-d @test-user-token.json \
http://192.168.2.110:8200/v1/auth/token/create | jq
And we created a new root user with the token s.3ionpxkpnV7FWR709o8JS4uo and username test-user
{
"request_id": "7ad054c1-c7a1-5c2c-f83f-a0d2ab756e4f",
"lease_id": "",
"renewable": false,
"lease_duration": 0,
"data": null,
"wrap_info": null,
"warnings": null,
"auth": {
"client_token": "s.3ionpxkpnV7FWR709o8JS4uo",
"accessor": "u8op0uCIPHuqgHhDJ59SVEW9",
"policies": [
"root"
],
"token_policies": [
"root"
],
"metadata": {
"user": "test-user"
},
"lease_duration": 3600,
"renewable": true,
"entity_id": "",
"token_type": "service",
"orphan": false
}
}